The Zero Trust Solutions
Recognizing new attack surfaces…
The Solar Winds and Exchange hacks highlight the cybersecurity risk and the dynamic attack surface in the enterprise ecosystem. The Zero Trust model maps out themes that enterprises can leverage as a blueprint for action.
A Fortune 2000 company sought to implement a cost-effective Zero Trust security program.
IOvations discovered during our Policy Review and System Health Check that this client needed to take critical steps towards a more robust security approach that aligned with their IT budget. Read the full case study here.

Tailoring the approach
Cloud usage is increasing, placing a premium on visibility and security controls. Endpoint and mobility strategies are essential and having context into events via analytics are all areas of our expertise, with best-in-class solutions and services. Our Oventium security experts focus on critical domains across your enterprise ecosystem.
Zero Trust Workshop
IOvations Zero Trust experts will conduct a workshop to map your security program today from a policy, technology, architectural, and operational perspective.
Zero Trust Action Plan
The journey towards Zero Trust is anchored on five themes:
- Defining the attack surface
- Visibility into your transaction flows
- Planning and maturing towards a Zero Trust Architecture that is customized to map to your business needs
- Instituting a Zero Trust policy centered around the who/what/where/why
- Monitoring – extensible solutions that can continuously review logs and generate an actionable yield on alerts
Putting these five themes into action requires fully understanding your business mission and tailoring an approach to achieve the outcomes that best fit your organization.

These themes are a beacon to drive effective planning, action, and execution. Our clients benefit from a collaborative approach rooted in the extensible capabilities in a broad range of leading IT solutions. More importantly, we provide actionable steps, insights, and pragmatic guidance on refining focus and execution along the Zero Trust Journey.
Wherever you are in your journey to Zero Trust, our security experts can help. We can assist in technology selection, implementation, policy refinement/development, or conduct a workshop if you are in the early stages of your journey.
Arrange a meeting with IOvations to discuss your goals and leverage our experience in driving Zero Trust across a broad range of enterprise clients. Our mission is to focus on your success!
We offer tailored security service engagements ranging from upgrades to design to migration, focusing on delivering on the requirements that will accelerate your security and operational effectiveness.
Our comprehensive and collaborative approach involves your key stakeholders to better understand security needs and objectives, which technologies to leverage, operational processes, and the financial impact on your organization.
Take the Zero Trust Journey With Us and Secure IT Now!
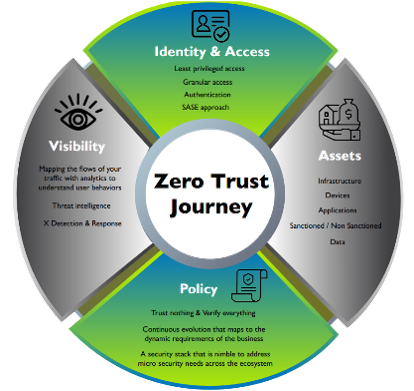
Identity and Access
- Starts with the least privileged access
- Granular access
- Authentication
- SASE approach
Assets
- Infrastructure review
- Devices
- Applications
- Sanctioned/Non-Sanctioned
- Data
Policy
- Trust nothing and verify everything
- Continuous evolution that maps to dynamic requirements of the business
- Security stack that is nimble and addresses micro security needs across the ecosystem
Visibility
- Mapping flows of your traffic with analytics to understand user behaviors
- Threat intelligence
- X detection and response
Take the Zero Trust Journey With Us and Secure IT Now!
Identity and Access
Starts with the least privileged access | Granular access | Authentication | SASE approach
Assets
Infrastructure review | Devices | Applications | Sanctioned/Non-Sanctioned | Data
Policy
Trust nothing and verify everything | Continuous evolution that maps to dynamic requirements of the business | Security stack that is nimble and addresses micro security needs across the ecosystem
Visibility
Mapping flows of your traffic with analytics to understand user behaviors | Threat intelligence | X detection and response
