Advisory Services
Our experienced security advisors can help you implement a Zero Trust strategy that starts with identifying and assessing your current cybersecurity systems and operational approach.
We offer project-specific engagements ranging from security program development to security controls required for compliance and full-blown security modernization across the enterprise ecosystem.
The centerpiece of our engagements is our security best practices that are pragmatic and focused on enabling your business needs.
Secure IT Now with Value & Experience You Can Trust
Cybersecurity is in our DNA! SECURE IT NOW is our mantra, and engaging clients with readiness is our mission. Security is imperative, but enablement drives business. We have over ten decades of collective expertise that has consistently enhanced, transformed, and optimized security effectiveness. SECURE IT NOW with IOvations—readiness that scales and performs.
Trusted Advisors
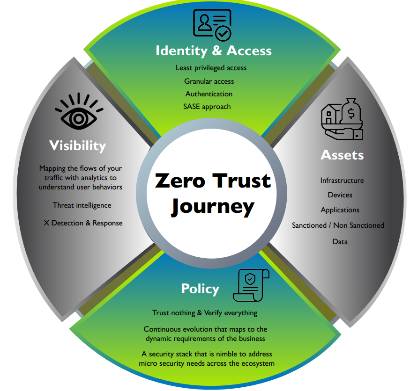
Many IT security leaders embrace Zero Trust as a practical approach to managing cyber-related challenges.
Implementing a Zero Trust Strategy is complex, and the journey starts with identifying and assessing your current cybersecurity systems and operational approach.
Let our experienced advisors take you on the Zero Trust Journey.
Project Planning
We understand that time to market means everything to our clients, and we have expert resources with the experience of being a consumer in high-performance environments. Best practices, execution, and accountability with your success is our goal!
Before we determine what needs to be upgraded or migrated, we do intensive performance testing to make sure everything is working at the required level. We’ll test both your hardware and your software to ensure the end-user is getting the best possible experience.

CISO as a Service
Today, Chief Information Security Officers (CISO) has a much broader range of responsibilities than traditional IT security roles. Over the past few years, we have seen the emergence of our CISO as a Service.
Our CISO as a Service offers Program Development, Compliance, Governance and Risk, and Cybersecurity Readiness and Awareness. We can continue executing numerous new requirements as a collaborative extension of the CISO to support software security, cloud applications, security awareness, training, and project execution.
Health Checks
Our security advisors will conduct a thorough rule review when providing and establishing data security, cloud security, and network security management for your company. We examine firewall rules within each policy for effectiveness and appropriateness.
We also review and evaluate the most current software and updates to establish their ability to meet your needs, providing a detailed evaluation of the health and security of your system when the analysis is complete.


Assessments
- Penetration
- Cloud Security
- GRC
- Incident Response
- Security Awareness
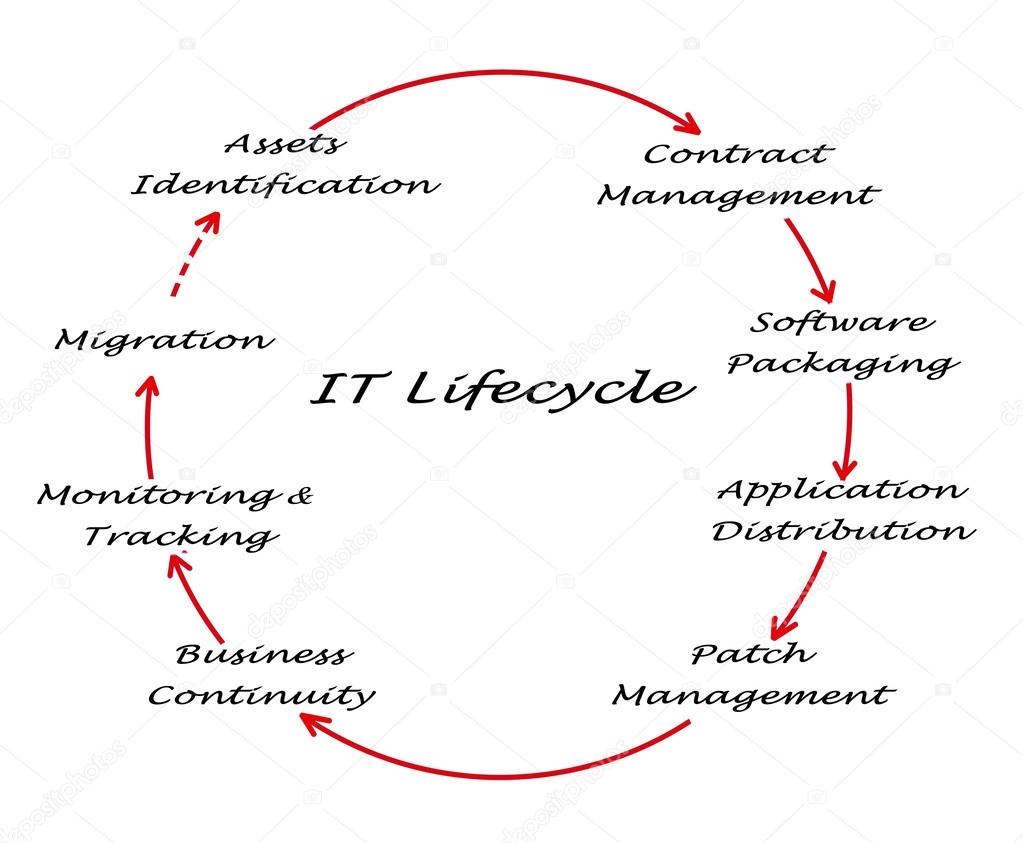
IT Lifecycle Management
We will work with you and your staff to develop a scalable and reliable security solution, from design to implementation, optimization, and documentation to ensure a continuous, safe environment.
As we work together and build our relationship, we continue to provide upgrades, patches, and other major releases for your hardware and software. Your IT Lifecycle subscription will address certifications, critical upgrades, and more.